 Last updated July 3, 2020
Last updated July 3, 2020
This is a technical guide for increasing community safety and security when using Zoom Meetings for public or semi-public events. The Zoom Meeting platform is designed to allow fairly full participation by all meeting participants, rather than being designed for webinars or presentations where only some people are invited to speak or share content. Therefore, many of the tips included here are meant to help you configure Zoom meetings to make it more like a webinar, with more centralized control for meeting hosts.
Also see our blog post on Zoombombing and digital community security for additional background info and context.
We have written this guide specifically for Zoom because of how widely it is used both generally and in our movements. However, this is not an endorsement of using Zoom, especially given serious cause for concern about Zoom's willingness to limit security in order to work with law enforcement. While the technical details in this guide are specific to Zoom Meetings, much of the guide can be adapted for use with other similar video conferencing platforms, including Jitsi Meet, which is open source and can be self-hosted as movement-owned infrastructure by trusted political organizations, as on https://meet.mayfirst.org. These and other options should be considered when choosing the appropriate platform for a given situation. For more guidance, see this guide to choosing a video conferencing tool from Martin Shelton at Freedom of the Press Foundation.
This guide draws significantly from the What is “Zoom Bombing?” Media Manipulation and Sociotechnical Vulnerabilities webinar presented on April 3, 2020 by Joan Donovan, Gabby Lim and Brian Friedberg of the Technology and Social Change Research Project at the Shorenstein Center.
Determining what's needed
The safety team, or the person or people responsible for safety and security during the event, should begin by asking some basic questions about the event being planned:
- What is encouraged, allowed, expected and/or tolerated from attendees during the event, and what isn't? Will the community be actively participating, or only watching or listening? Should attendees be able to share their screens or files, enable their video or unmute themselves, with or without permission from event hosts? Can attendees ask questions either aloud or via chat at any time, or only during designated times? How much debate and cross-talk is appropriate in the space?
- What are probable threats to the event and the community gathered for it, and how likely is it that those threats will occur? Different events and communities face different risks based on who is participating, what the topic matter is, how public the event is, and other factors. The security team should have a good idea of what to expect, including what has happened during past real-life and virtual events and any new, special or timely concerns.
- How does the community or the organization wish to respond to threats that materialize during the event? Should attendees be allowed to use video, audio, chat, file-sharing or screen-sharing at all during the event? If yes, should disruptive individuals be removed from the event immediately, or muted and approached in attempted deescalation? Does the appropriate approach depend on who is doing the disrupting or the nature of the disruption?
The answers to these questions should be used to determine how the Zoom meeting is configured and managed before and during the event.
Some of the Zoom settings discussed here can be set as the default for all meetings created using a given account by logging into the Zoom.us web portal and changing the Meeting settings for the entire account. Other settings are configured on a meeting-by-meeting basis when creating meetings, and still others can only be set once the Zoom meeting has begun.
The instructions below are written specifically for the Zoom web portal as it exists today, but most of the instructions translate easily to the Zoom apps on desktops, tablets, phones and other devices.
Before the event
Raise barriers to entry
After you determine how public or private a given event needs to be, you should then raise the barriers to entering the Zoom meeting as much as possible without making it too difficult for people to participate.
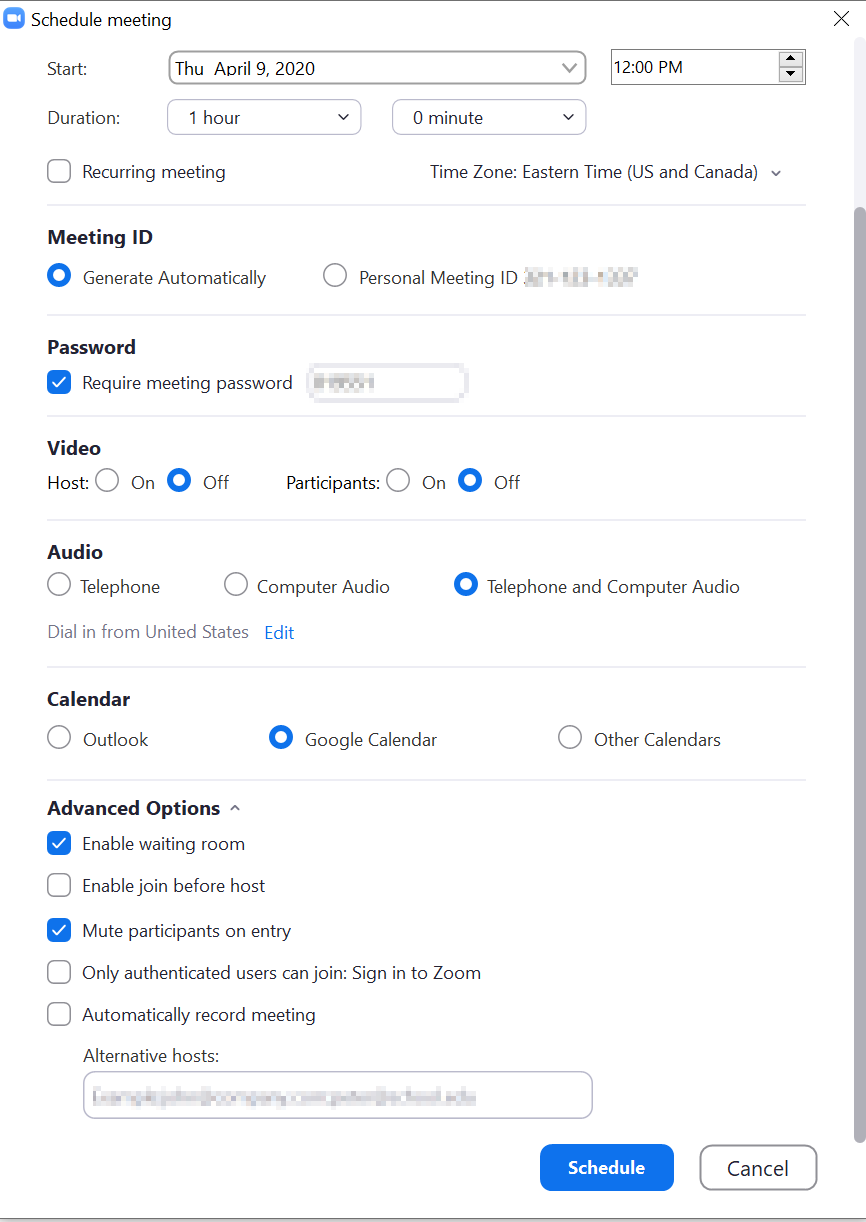
The most important barrier to entering a Zoom meeting is access to the meeting link or the 9-10 digit meeting ID that is included in meeting links. No one can get into a meeting without the link or the meeting ID, so the more widely the link or ID is shared, the more likely you are to be Zoombombed. Sharing a Zoom link on your website or via social media is an effective way to get the word out, but it also makes it very easy for Zoombombers to find your link and target your event.
Instead, for semi-public or public events, consider requiring some sort of event registration before sharing the Zoom link directly with participants. Zoom Meeting includes a built-in registration option for licensed (paid) accounts, but you could set up a separate registration through your own event management system, through a simple webform on your organization's website, or even by having people email you to sign up before you share the meeting link with them.
Remember that sharing your Zoom account Personal Meeting ID (or PMI) is TMI! The personal meeting ID allows you to quickly connect to what amounts to a never-ending Zoom meeting for the linked account, which is useful for internal organizational meetings but should not be shared beyond that. Also don't reuse automatically generated meeting IDs that you've used or shared in the past, especially if Zoombombers or other intruders have previously crashed those meetings.
Instead, be sure to automatically generate a meeting ID for each public meeting; when on the scheduling a new meeting or editing an existing meeting, find the Meeting ID setting and select the "Generate Automatically" option.
You can also require that participants log into a Zoom account before they can join your meeting, rather than only needing to click a link or enter the meeting ID, thus putting up another deterrent for would-be Zoombombers. When scheduling or editing a meeting, select the "Only authenticated users can join" option in the Meeting Options section (called "Advanced Options" in Zoom desktop apps.)
Only do this if you're comfortable requiring that all participants set up their own individual Zoom accounts and log in with them before joining the call, which is a significant barrier to entry!
The Waiting Room feature places participants into a virtual waiting room when they join the meeting; from there, hosts can choose to allow participants into the meeting either one-by-one or all at once. The Waiting Room feature must first be enabled for the Zoom account in use via the web portal. Then you can either select the "Enable waiting room" option under Meeting/Advanced Options when scheduling or editing individual meetings. During a meeting you can also use the "Enable Waiting Room" option in the Security button menu to choose to enable a waiting room on the fly for a meeting already in progress.
Finally, you can set meeting passwords by selecting the "Require meeting password" option when scheduling or editing meetings. A numerical password will be automatically generated but can be customized if you'd like. For best results, share the meeting link or ID separately from the meeting password; if they are both posted in the same place or shared in the same email, a potential intruder could get both pieces of information needed to access the meeting at once.
Centralize control
There are a few settings you should check to properly grant the right permissions to participants once they've joined the meeting. Configure these settings based on the different kinds of communication and participation that you earlier determined are needed for your event.
These settings are available when scheduling or editing individual meetings:
- Begin the meeting with all participants' video turned off and audio muted. In the Video section, set Participants to "Off." Under Meeting Options/Advanced Options, select "Mute participants on entry."
- Zoom's default is to prevent participants from joining meetings before the host(s), but you can double-check that the "Enable join before host" option under Meeting Options/Advanced Options is not selected so that participants can't join until after a host has started the meeting.
- If you'd like to add alternative hosts to a meeting ahead of time so that other Licensed users on the same Zoom account can also start the meeting and manage participants, enter the email addresses associated with their Zoom accounts in the "Alternative Hosts" field under Meeting Options/Advanced Options.
There are additional settings that can be preset for all meetings created by the account via the Meeting tab of the Settings section of the Zoom web portal:
- The account-wide defaults for many of the settings above can be set via the web portal; those defaults above can be overridden for individual meetings.
- Screen sharing should be restricted to hosts only for public events, especially since screen sharing is how Zoombombers tend to display their offensive or disruptive content. In the "Screen sharing" section, select "Host Only" for both the "Who can share?" and "Who can start sharing when someone else is sharing?" options.
- Consider disabling private chat between participants, which can be used to send inappropriate or abusive content to participants without the hosts seeing. Under "In Meeting (Basic)," toggle the "Private chat" option off.
- Also under "In Meeting (Basic)," double-check that the "File Transfer" option is toggled off to prevent both participants and hosts from sending files through the in-meeting chat.
- Double-check that the "Allow removed participants to rejoin" option is disabled, since that allows removed participants (e.g. Zoombombers) to join again after they've been removed from the meeting.
At the start of the event
Be sure to start the Zoom Meeting early! Fifteen or twenty minutes will allow facilitators, safety team and key participants to connect, test their audio and video, and make sure the meeting is configured properly. Other participants will also be able to join as soon as the meeting has been started by a host; if your meeting isn't configured to use a Waiting Room as described earlier, you can either put early participants On Hold as described below or you can simply accept their presence and let them know that you'll be starting soon.
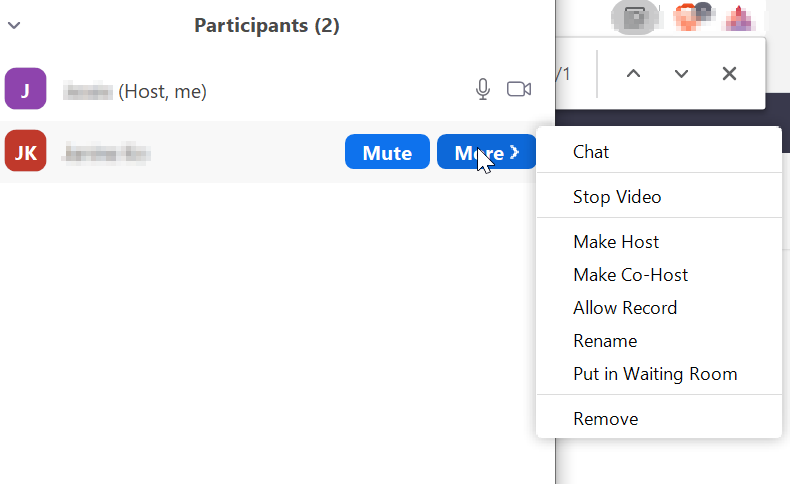
All members of the safety team should be the host or co-hosts of the Zoom meeting so that they can manage participants and technical configuration during the event. To make someone a co-host after they've joined the Zoom meeting, the meeting host should right-click on their image in the Gallery View or hover over their name in the Participants window and click the More button, then click "Make Co-Host." ("Make Host" will switch to that person being the host instead of the current host, rather than making them a co-host, which is useful when the current host needs to disconnect but the meeting should continue.)
The safety team should review a number of settings before the event starts to make sure they match up with what's needed for this particular event, as determined earlier.
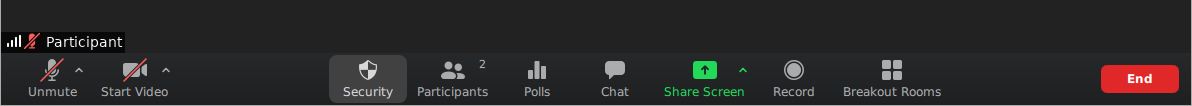
In response to increased public concern about Zoombombings and other security issues on the platform, Zoom has added a Security button at the bottom of the main Zoom window. This button provides quick access to a number of useful security-related settings, most of which are also found elsewhere in the Zoom interface: Lock Meeting; Enable Waiting Room; Allow Participants To Share Screen, Chat or Rename Themselves; Remove Participants; and Report. These settings are described in greater detail below. The safety team should be familiar with those handy options that can be used to quickly deal with problems that may arise during the event.
Click the "Manage Participants" button towards the bottom of the main Zoom window, then review and adjust these settings as needed:
- Click the "Mute all" button at the bottom of the Participants window to mute all current and new participants. You can also uncheck the "Allow Participants to Unmute Themselves" box to prevent non-co-hosts from speaking or otherwise making noise during the event unless a co-host specifically unmutes them.
- Click the three dots ("...") button at the bottom of the Participants window, then select "Play Enter/Exit Chime" so that a sound is played when new participants join, making it easier to quickly spot intruders (but also adding possibly distracting "dings" to the event!)
- You can also select "Mute participants on entry" in that menu, though if you've already used "Mute All" that shouldn't be necessary.
- After either a certain period of time or after all participants have joined the meeting, use the "Lock Meeting" option in the three dots ("...") menu to prevent any new participants from joining. Meetings can be unlocked and locked again as needed. "Lock Meeting" is also available via the Security button at the bottom of the main Zoom window.
Next, review the screen sharing options to ensure they match what's needed for the event. Click the upward-pointing arrow next to the Share button at the bottom of the main Zoom window to open the "Advanced Sharing Options..." pop-up and review the settings for "Who can share?" and "Who can start sharing when someone else is sharing?" For public events, both should be set to "Only Host."
Finally, click the Chat button at the bottom of the main Zoom window to open the "Zoom Group Chat" window. Click the three dots ("...") button to review the "Allow attendees to chat with" options and properly set whether attendees can publicly or privately chat with each other. Most public events should set this to "No One" or "Host Only" to avoid inappropriate text content being shared between participants.
Note that the options above can also be changed during the event itself, either because conditions have changed or because certain parts of the event require or allow more audience participation than others.
During the event
The safety team should remain in the meeting for the entirety of the event to deal with any disruptions as decided earlier, as well as to help presenters and participants with any technical issues related to the way settings have been adjusted for meeting security. The safety team should ideally not be performing other roles during the event, including facilitation, presentation or even active participation. This allows the safety team to focus on watching for signs of Zoombombing or other unwanted or inappropriate behavior and dealing with it as quickly as possible so that the event can continue.
Safety team members should select the Gallery View and make their main Zoom window as large as possible so that as many participants are visible on screen at once. The current active speaker's thumbnail is highlighted in yellow, making it easy to spot who is currently or was most recently making the most noise while unmuted. The safety team should also have the Participants window open, allowing them to easily see who has joined the meeting. The microphone and video camera icons in the Participants list show whose audio or video are turned on and whose audio is currently active. Safety team members should also have the "Zoom Group Chat" window open throughout the event (if participant chat is enabled) to monitor for any inappropriate content or respond to questions or requests from participants, presenters and other safety team members.
If the Waiting Room feature described earlier is in use for the event, the safety team should monitor the waiting room and allow newly joined participants in at the appropriate time, either one-by-one or en masse.
At the beginning of the event, share the community guidelines, ground rules and expectations for participation with all participants so that they understand what's expected and why certain functionality might be disabled.
If disruptions do occur, the safety team should respond to them as quickly as possible to reduce the damage done and allow the event to continue as seamlessly as possible. Responses to disruption should be as calm and quiet as possible so that you do not "feed the trolls" by giving them what they want: a disrupted event with people visibly and audibly upset.
Possible responses to disruptions include:
- Turn video off for a participant by hovering over their name in the Participants window, clicking the More button, then clicking "Stop Video." The participant will not be able to start their own video again unless they leave and rejoin the meeting. This is currently the only way to stop participant video -- there's no way to entirely disable video for all participants or non-hosts.
- Mute an individual participant by hovering over their name in the Participants window and clicking the Mute button. They will still be able to unmute themselves unless you use the "Mute All" button and uncheck the "Allow Participants to Unmute Themselves" box.
- If many participants are disrupting the event via audio, or you're not sure who is disrupting, mute all participants (including hosts and co-hosts) by clicking the "Mute All" button at the bottom of the Participants window. Uncheck the "Allow Participants to Unmute Themselves" box before clicking the Yes button so that only hosts and co-hosts will be able to unmute themselves or others.
- If deescalation is an appropriate response to a given disruption, chat privately with individual participants to explain the ground rules for the event and ask them to adhere to them. Use the To: button in the "Zoom Group Chat" window to choose whether to chat publicly with all participants or privately with a specific participant. This response is not recommended for Zoombombing! It is a good option to consider if the disruption is coming from people folks know, community or organization members, or others whose continued inclusion in the space would be ideal and who would likely respond well to such intervention.
- Temporarily remove participants from the event by putting them on hold, which puts them in a waiting room even if one isn't in use for your call. Hover over the participant's name in the Participants' window, click the More button, then click "Put on hold." While on hold participants remain connected to the meeting but cannot participate, listen or watch. Although Zoom indicates that hosts and co-hosts can send messages to participants who are in the waiting room, we've tested this and those messages are not visible to participants, so further deescalation would need to take place outside of Zoom.
- If all else fails or if the disruption warrants it, remove participants from the Zoom meeting entirely. Hover over the participant's name in the Participants window, click the More button, then click Remove. A pop-up will appear that explains whether the participant will be able to rejoin the meeting or not, which is based on the "Allow removed participants to rejoin" option in the web portal Settings for the account, described earlier. "Remove Participants" is also available via the Security button at the bottom of the main Zoom window.
- You can also choose to report the disruption to Zoom using the Report option in the Security button menu while the event is still in progress; see below for more on the Report option.
After the event
As with in-person events, the safety team should debrief together after the event, either separately as a team or together with other event organizers. During the debrief, discuss how things went, what went right, what went wrong, and how you plan to bring any lessons learned forward to change how you plan for safety and security at future events.
If the event was Zoombombed or similarly disrupted by intruders, there are steps you can take to better understand what happened and prevent it from happening again in the future.
- Again, don't feed the trolls! Refrain from reacting in an upset or angry manner in the moment or publicly if possible; though that's easier said than done, it avoids giving the trolls the lulz they're looking for.
- Gather evidence of what happened so that you can understand it better and take any further action more easily. Such evidence includes screenshots that safety team members or other participants took during the disruption, including screenshots of the participant list; the chat logs from the call; and the Zoom recording, if the meeting was recorded.
- Report the incident to your tech support providers, if you have them, so that they can assess whether any further actions should be taken to address ongoing digital security for your organization.
- Report the incident to Zoom via their support form or the Report option in the Security button menu at the bottom of the main Zoom window. Zoom has rightfully been the target of scrutiny about the security, privacy and safety of their platform and should be made aware of violations of their terms of service so that they are further encouraged to take action to prevent such abuses in the future. That said, we aren't familiar with how Zoom handles these reports or how they interact with users who file reports or are reported and cannot guarantee that the experience will prove pleasant or fruitful!
- If information for the meeting was shared publicly, remove all Zoom links for future events from public postings on websites, social media and calendars to prevent those events from being targeted. You should also change the Zoom links themselves so that new Meeting IDs are generated for the future events.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.